TryHackMe CTF: Brooklyn Nine Nine
TryHackMe: Brooklyn Nine Nine CTF
Today, we are going to walkthrough the Easy rated TryHackMe room, "Brooklyn Nine Nine." This was an extremely fun room, and as fan of the show, I was excited to get this machine started. Lets dive in!
Enumeration
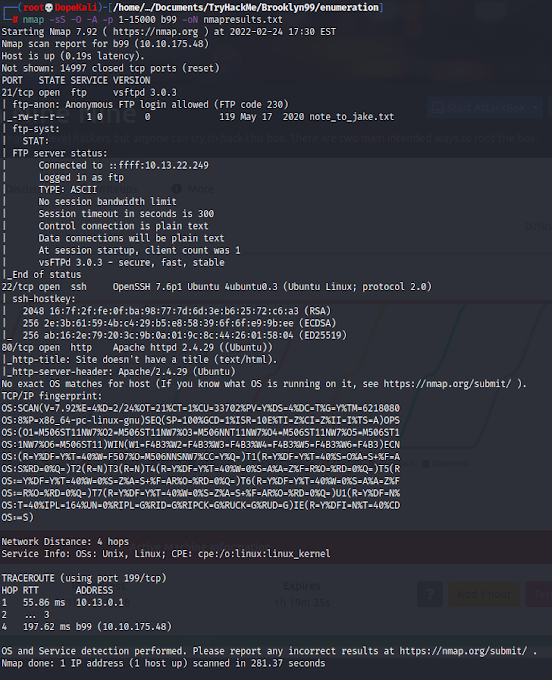
Let's start out by adding this machine to our Hosts file, then running our Nmap scan.
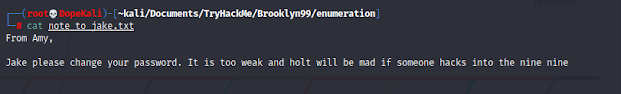
Okay, so we have FTP, SSH and a web server running on this machine. The first thing that jumps out is the Anonymous login for FTP, with a readable text file called "note_to_jake." Let's go grab that
Now that we have the file, we read it and see that it's a note from Amy telling Jake to change his password to something stronger so Holt doesn't get mad if B99 gets hacked.
We have 3 possible usernames here, Jake, Amy and Holt. Let's keep this aside for now and head to the web server.
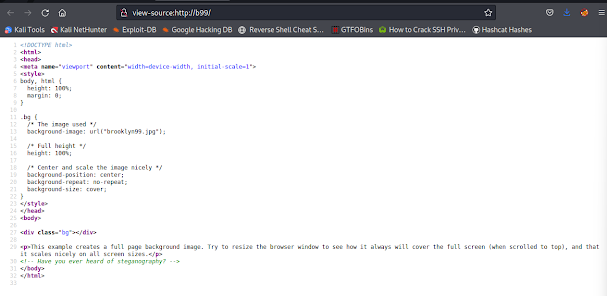
Once we get to the web server, we see just a picture of the Brooklyn Nine Nine cast. First thing I always do is check the source code.
Immediately we see a note that was left asking if we've heard of Steganography. Okay, so there is clearly something hidden in that picture on the web servers main page. We can use the URL listed in the source code above to navigate to the source of the image to download it.
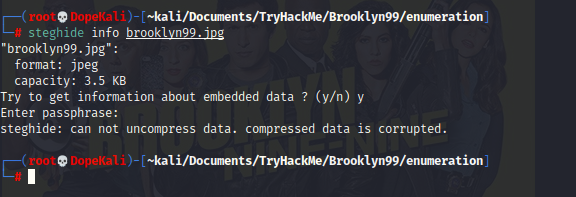
I use a tool called Steghide to see if I can see what's hidden in this image, but find out that it's password protected.
We can use a tool called Stegcracker to see if we can crack this password. I'm just going to use the standard RockYou.txt to attempt this first. After a few minutes, we can see that Stegcracker was able to successfully crack the password
Awesome, so let's go back and use Steghide to extract the data inside this file now that we have the password.
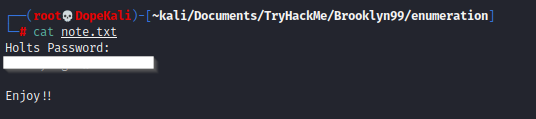
Okay so we have another text file called "note.txt" and if we read this, we can see we have a confirmed username along with a password!
Exploitation
The exploitation of this machine is very simple. The first thing I did was attempt to use the username/password to SSH into the machine
Success! Let's go grab the user flag!
Post-Exploitation
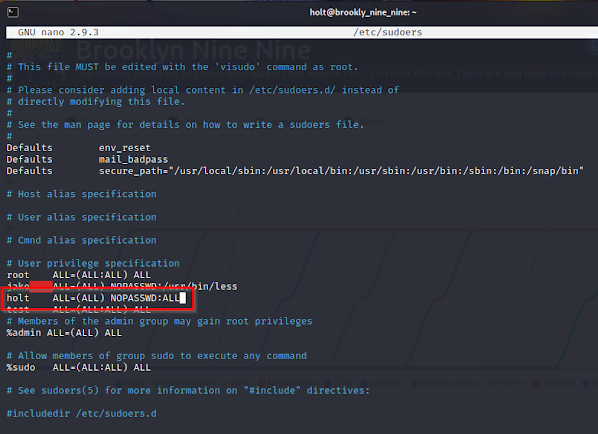
So since we have Holt's password, let's just run a sudo -l command and see if we can run anything as root without a password.
Okay, so we can run Nano as root without a password. Being able to run Nano, a text editor, as root means we can edit any file we want as root as long as we use the Nano editor. If we can do that, why not just attempt to change the Sudoers file to allow holt to run anything as root, without a password?
Conclusion
Overall, this was a very simple, yet really fun box! I am glad I was able to stumble across this box as again, I'm a huge fan of the show! Hopefully this guide provided some help if you were stuck!